Watchdoc - Secure port 5744 using a signed certificate
August 2025
Principle
In version 6.1.1, exchanges between the IIS* web server (whether local or remote) and the Watchdoc kernel pass through port 5744 using the HTTPS protocol (TLS 1.3).
As the TLS protocol requires a certificate to authenticate the server and establish a secure communication channel, v. 6.1.1 includes a self-signed Watchdoc certificate by default: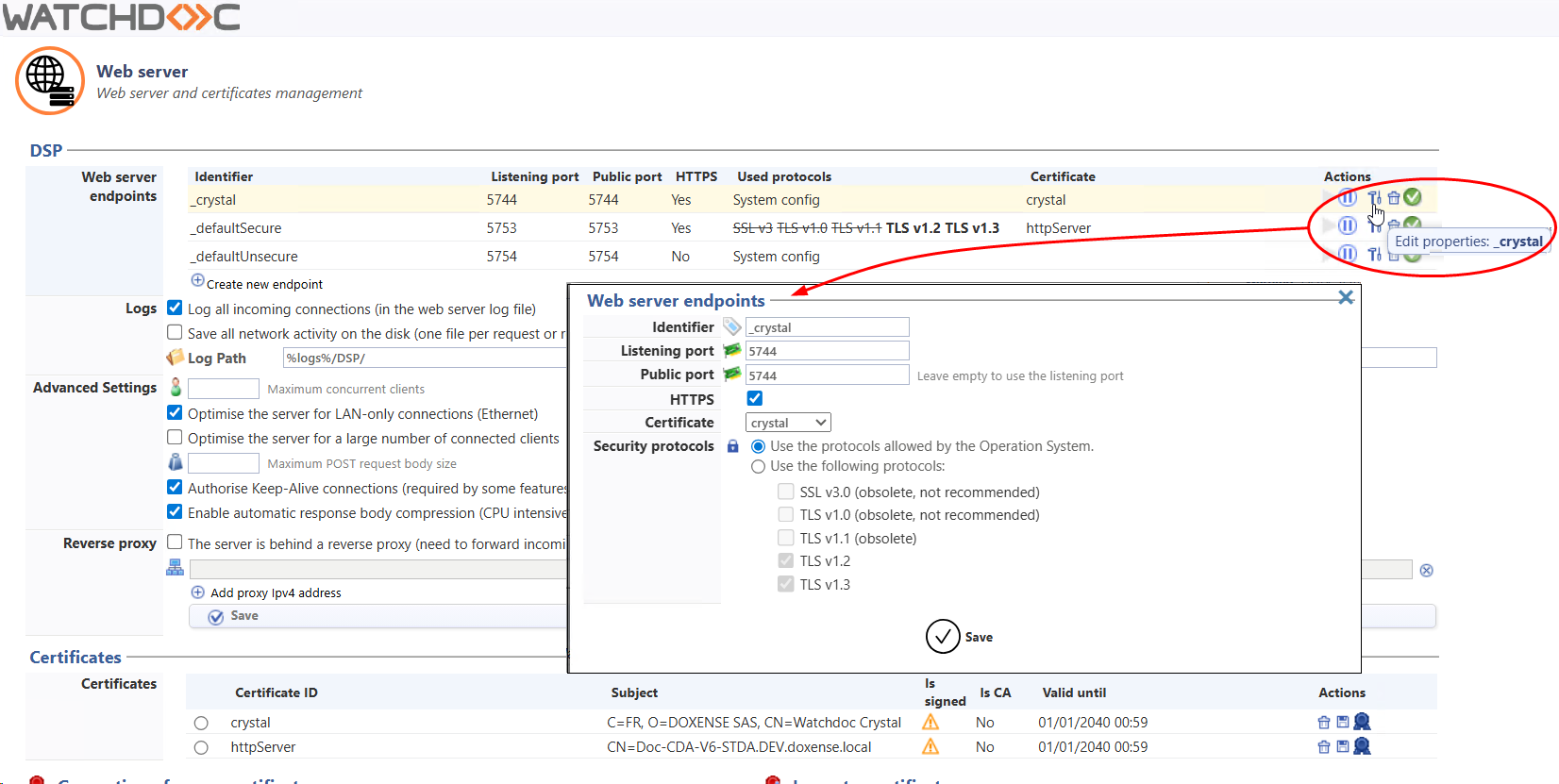
If you wish to increase the security level of your Watchdoc server using a certificate signed by your certification authority, you can follow the procedure below.
Note: If you created a ‘Website entry point’ with the identifier ‘_crystal’ using a port other than 5744 in a previous version, your configuration will be retained when you update to 6.1.1.
Procedure
To assign a CA certificate to port 5744:
-
request a certificate from your domain-trusted certification authority;
-
import the CA certificate into Watchdoc (see Importing a signed certificate);
-
associate this certificate with port 5744;
-
in the Certificates section of the Watchdoc administration, for the signed certificate you just added, check that the Is signed parameter displays the logo
 ;
; -
access the server hosting the Watchdoc master as an administrator;
-
open the server* registry;
-
open the Software > Doxense > Watchdoc folder;
-
create a CertificateValidationMode key and fill in the following values:
-
Name: CertificateValidationMode
-
Type: dword
-
Data: 1 (this value means ‘AuthorizedByMachine’);
-
-
save the changes made to the registry;
-
go to the website to check that the certificate is working properly.
N.B.: It is possible to sign the default ‘crystal’ certificate (click on  Sign this certificate). In this case, it is essential to retain the initial 'subject' of this certificate, which must remain unchanged after signing.
Sign this certificate). In this case, it is essential to retain the initial 'subject' of this certificate, which must remain unchanged after signing.