Principle
In Watchdoc, Guest management allows you to manage a database in which Guests, users who are not registered in the Watchdoc directory, are recorded. To obtain precise information about users in the Watchdoc print history, you need to configure the confidentiality settings on the print device.
Access the device configuration interface as an administrator.
-
From the WSC Main Menu, click on the Configuration menu item:
-
In the Advanced Configuration interface, click on the Guest Base button;
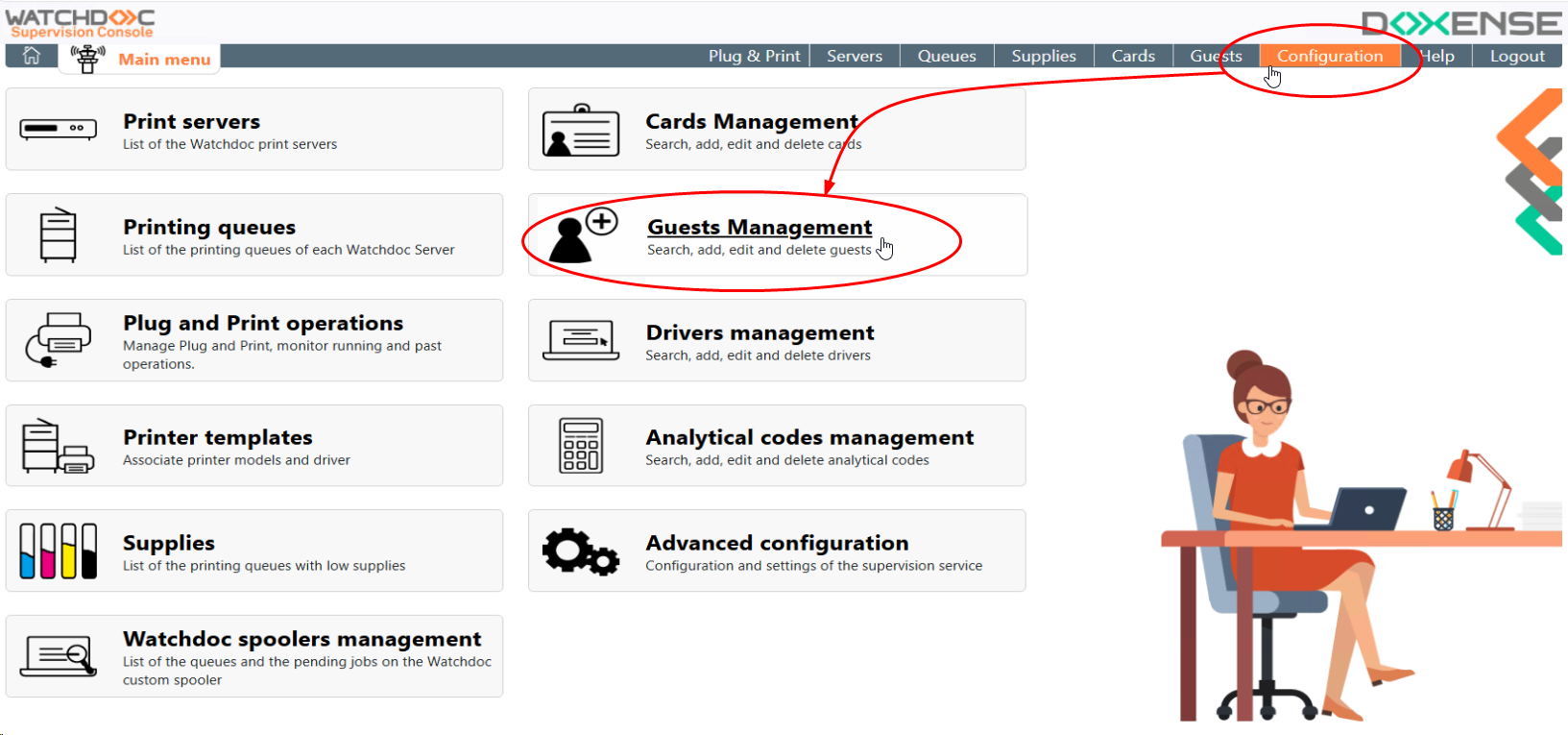
è This takes you to the Guest database configuration interface.
Configure the guests database
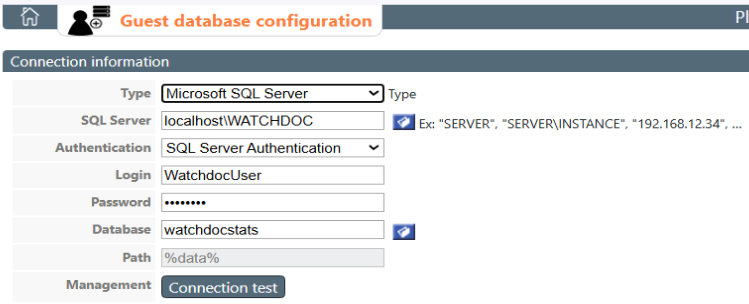
Connection information section
-
In this section, enter the information needed to establish the connection with the database in which the guest accounts are stored:
-
Type: select the type of database used to register guest accounts from the list;
-
SQL server: In this field, specify the server on which the database used to register guest accounts is located. If you don't know the name of the server, click on the button
 to browse the list of existing servers and select the server used.
to browse the list of existing servers and select the server used. -
Authentication: select the type of authentication required to access SQL Server (SQL Server or Windows SSPI).
-
User name: if you have opted for SQL authentication, enter in this field the user name authorised to access the database used; if you have opted for SSPI authentication, this information will be communicated automatically.
-
Password: if you have opted for SQL authentication, enter in this field the password associated with the user authorised to access the database; if you have opted for SSPI authentication, this information will be communicated automatically.
-
Database: in the field, enter the name of the database used to register guest accounts.
-
Path: if the database is SQLite, enter the path to the database :
-
-
Once all the fields have been completed, click on the Connection test button to check that the information to check that the information provided allows access to the database used to register guest accounts.
Automatically generated PUK code
The guest can use a PUK![]() (Print User Key). In Watchdoc, this is a code (associated with a user account but used alone) sufficient to allow the user to authenticate in a WES.
The PUK code is generated thanks to an algorithm. The user can consult it in the "My account" page of Watchdoc.
For security reasons, we advise against using the PUK code and recommend using a login (user account)/PIN code. code or a PIN
(Print User Key). In Watchdoc, this is a code (associated with a user account but used alone) sufficient to allow the user to authenticate in a WES.
The PUK code is generated thanks to an algorithm. The user can consult it in the "My account" page of Watchdoc.
For security reasons, we advise against using the PUK code and recommend using a login (user account)/PIN code. code or a PIN![]() The PIN (Personal Identification Number) is a code with at least 4 digits. It is used, for example, on a cell phone or smartphone equipped with a SIM card. In Watchhdoc, it is a code which, combined with the user name, constitutes a means of authentication on a WES.
Deduced from the AD, the user can consult it in his My Account page.
It is stored either in a SQL table or in a Json file, and can be stored as is or secured by hashing.
Translated with DeepL.com (free version) code to authenticate themselves in Watchdoc. These codes are entered in the guest account creation interface. If these codes are not entered manually, they are generated automatically when the guest account is validated.
The PIN (Personal Identification Number) is a code with at least 4 digits. It is used, for example, on a cell phone or smartphone equipped with a SIM card. In Watchhdoc, it is a code which, combined with the user name, constitutes a means of authentication on a WES.
Deduced from the AD, the user can consult it in his My Account page.
It is stored either in a SQL table or in a Json file, and can be stored as is or secured by hashing.
Translated with DeepL.com (free version) code to authenticate themselves in Watchdoc. These codes are entered in the guest account creation interface. If these codes are not entered manually, they are generated automatically when the guest account is validated.
During generation, WSC adds the number 9 as a prefix to the PUK code in order to distinguish PUK codes from the Guest database from other existing PUK codes.
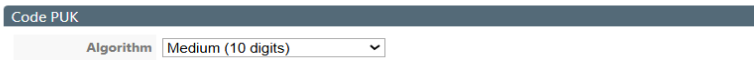
In this section, you specify the algorithm level to be applied when automatically generating the PUK code (when this PUK code is entered manually when creating the guest account, its length is not checked):
-
either a 7-digit algorithm (low security)
-
or an 11-digit algorithm (medium security):
èOnce the Guests database has been set up, you can add guest accounts to it.