CVE-2025-58384: remote code execution
Context
Vulnerability affecting Watchdoc versions lower than 6.1.1 allowing arbitrary remote code execution (RCE) in an unauthenticated and remote manner.
It is possible to perform remote code execution using an unauthenticated API call.
(cf. https://www.cve.org/CVERecord?id=CVE-2025-58384)
Impacts
Code execution on the print server. This at minimum allows compromising all printers (confidentiality breach) and retrieving the Active Directory account used by the print server.
Mitigation or remediation proposals
Mitigation: close remote access to port 5744 exposed by Watchdoc. For architectures with a remote IIS server, restrict access to this port to the remote IIS server.
Remediation: update to Watchdoc 6.1.1
CVE Description
| Vulnerability type | CWE - CWE-502: Deserialization of Untrusted Data (4.16) |
| Affected product(s) and version(s) | Watchdoc up to at least 6.1.0.5094 |
| Fixed version(s) | Watchdoc 6.1.1 |
| Attack type | Remote, unauthenticated |
| Vulnerability impact | Code execution, Denial of Service, Privilege escalation, Confidentiality breach, Information integrity breach |
| CVSS 4.0 Vector | CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H |
| CVSS 4.0 Score | CVSS v4.0 Score: 10.0 |
Mitigation procedure
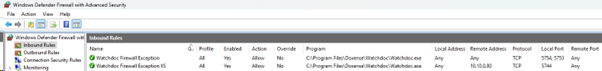
By default, Watchdoc adds a Windows firewall rule to allow all incoming connections.
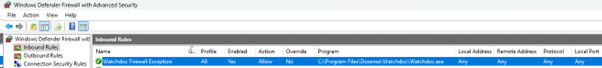
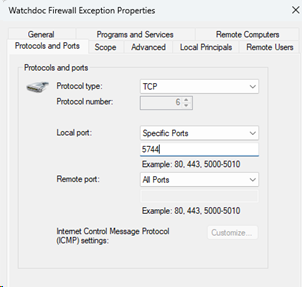
The mitigation consists of closing remote access to port 5744.
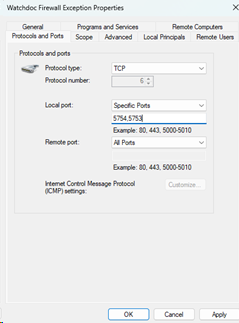
The proposed solution is to allow remote access only to ports 5754 and 5753.
To do this, edit the properties. In the “Ports and Protocols” tab, configure as follows:
The rule then becomes:
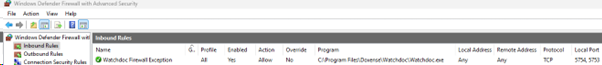
Note: ports 5754 and 5753 are the default Watchdoc ports. If they have been changed, their values must be adjusted accordingly.
Specificity for remote IIS
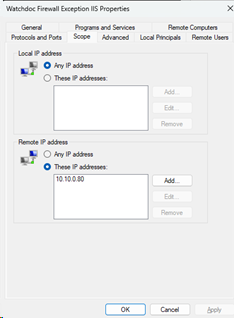
If the Watchdoc service and the IIS server hosting the Watchdoc administration are installed on different machines, access to port 5744 must only be allowed from the IIS server.
To do this, duplicate the previous rule.
Change the network port to allow only port 5744:
Allow remote connection only from the IIS server IP (example with 10.10.0.80):
The final configuration is as follows: